Embrace Control
We deploy a cost effective, practical approach to ATM Monitoring Management
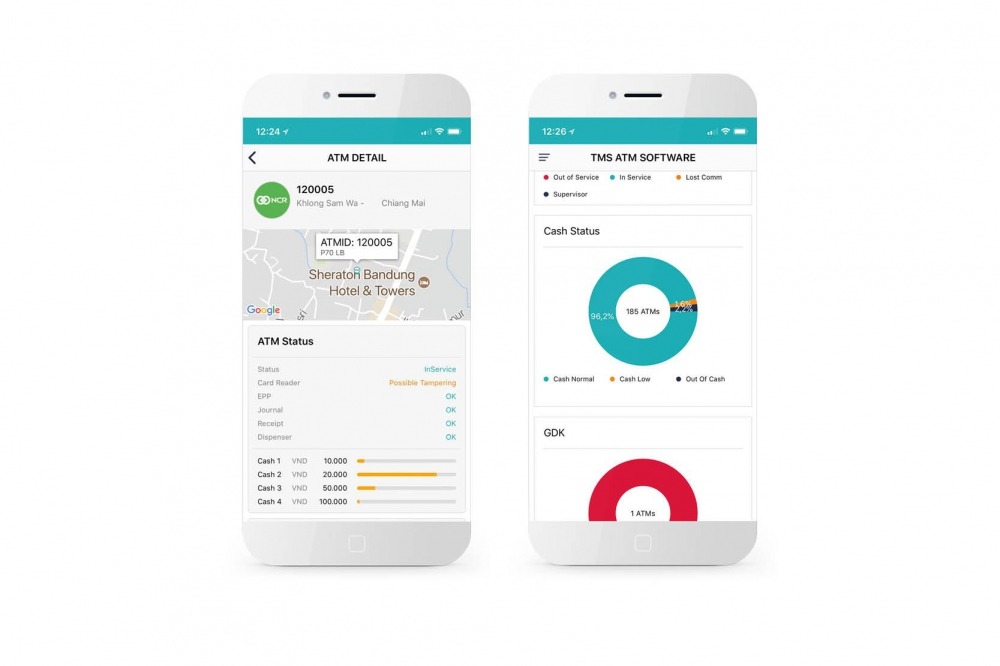
Our solutions provide what existing ATM management & monitoring solutions don’t: The ability to view the entire fleet of ATM & POS Machines, their current health status, analysis, Incident managment & period of maintenance in one look easy to use monitoring dashboard. Remote diagnostics provides instant insight into the state-
of-health of all ATMs, and the devices inside them from the sensor level.
A centralized dashboard view of all the ATMs in the network provides instant insight into real-time ATM status including security, for proactive prevention and resolution of incidents.
Customer expectations have soared. We deploy & maintain a converged system to wrap a suite of services around, including voice, video, messaging applications, collaboration, and more, delivering excpetional customer experience.
All calls can be extended to multiple user devices as smartphones, pcs while out of office thus no missed customer calls aka Computer Telephony Integration.
With ACD, we route incoming calls to the most appropriate agent in the office. Also acquire usage data such as call volume, calls handled, call duration and wait time etc & Route incoming calls to the proper queue and the right, available agent based on certain strategies we set up.
Paired with ACD, IVR prompts callers to their desired destinations with customized rules, helping SMEs handle high volumes of incoming calls to the most appropriate departments, greatly reducing customer dissatisfaction.
Keep track of every phone conversation to improve the performance of your agents or for compliance with regulatory requirements.


Migrating from old locks
Key-Less Access Management is the ATM industry’s first integrated key-less access management solution for ATM safe, top box, secure room and branch.
Our Security has integrated certified, state-of-the-art lock technology that is proven to be of the highest security specification, high-security HSM encrypted OTCs, mobile app, and central business server application for user and access schedule management
Benefits of The Key-Less Access Managment Solution
Building Bespoke Software Solutions.
Are you having a hard time deciding between custom software development and off-the-shelf software for one of the critical functions in your organization?.
We build custom software SaaS solutions to suit your organization. From simple notification systems, Mobile Apps, Web Apps & Web services
Protecting You Against Cyber Attacks
Can your security system handle an attack of sophisticated large volumes of malicious software?
We offer solutions ranging from end point security protection such as Antivirus, Antimalware, Antispyware & Network Firewalls.
We work with vendors such as Fortinet, Sophos, Kaspersky, McAfee, Panda Security, & Microsoft.We Deploy innovative tools that empower organizations to quickly and simply find the truth in any data in the digital world.
Our solutions empower investigators and forensic experts with the capacity to collect and analyze electronic data from smartphones, computer systems, networks, wireless communication & storage devices. Whether you are locked out of a smartphone, stranded with a ton of digital evidence gathered from crime scens, or just looking for a powerful forensic workstation to help you with investigations, we've got you covered
Whether you are a school, religious organization, non-profits, or any other community association, SMS Group messaging is an effective way of running projects by sending notices or notifications.
